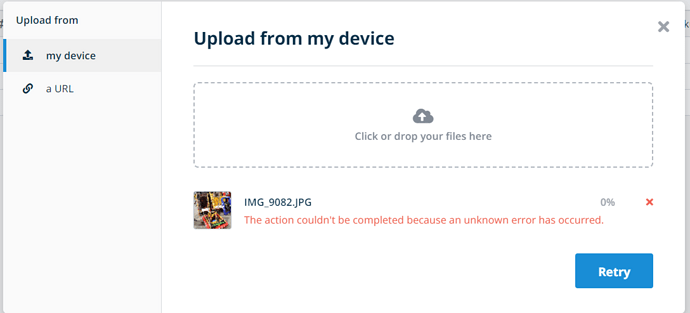
Hi @nigel
Thanks for trying to help me out.
Here is my Nginx Configuration, note that any entries that only contain “.hess” are for internal use only and are only for in the event my internet goes down.
#user nobody;
worker_processes 1;
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events
{
worker_connections 1024;
}
http
{
server_names_hash_bucket_size 64;
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
sendfile on;
#tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
gzip on;
server
{
listen 80 default_server;
server_name localhost;
#charset koi8-r;
#access_log logs/host.access.log main;
error_page 500 502 503 504 /50x.html;
location = /50x.html
{
#root html;
}
location /
{
error_page 404 /404.html;
}
error_page 404 /404.html;
# redirect server error pages to the static page /50x.html
#
# proxy the PHP scripts to Apache listening on 127.0.0.1:80
#
#location ~ \.php$ {
# proxy_pass http://127.0.0.1;
#}
# pass the PHP scripts to FastCGI server listening on 127.0.0.1:9000
#
#location ~ \.php$ {
# root html;
# fastcgi_pass 127.0.0.1:9000;
# fastcgi_index index.php;
# fastcgi_param SCRIPT_FILENAME /scripts$fastcgi_script_name;
# include fastcgi_params;
#}
# deny access to .htaccess files, if Apache's document root
# concurs with nginx's one
#
#location ~ /\.ht {
# deny all;
#}
}
server #Plex Internal Only
{
listen 80;
server_name plex.hess;
return 301 https://$http_host$request_uri;
#location /
# {
# proxy_pass http://localhost:32400;
# proxy_buffering off;
# proxy_set_header X-Real-IP $remote_addr;
# proxy_set_header X-Forwarded-Host $host;
# proxy_set_header X-Forwarded-Port $server_port;
# }
}
server #ISpy Public
{
listen 80;
server_name nvr.[REDACTED].net;
location /
{
proxy_pass http://localhost:8095;
proxy_buffering off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Port $server_port;
}
}
server #ISpy Internal Only
{
listen 80;
server_name nvr.hess;
location /
{
proxy_pass http://localhost:8095;
proxy_buffering off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Port $server_port;
}
}
server #Unifi Edge-OS Remote redirect to https
{
listen 80;
server_name routing.[REDACTED].net;
return 301 https://$http_host$request_uri;
#location /
# {
# proxy_set_header X-Real-IP $remote_addr;
# proxy_set_header X-Forwarded-Host $host;
# proxy_set_header X-Forwarded-Port $server_port;
# }
}
server #Baserow Internal Only
{
listen 80;
server_name br.hess;
ssl_certificate V:/fullchain2.pem;
ssl_certificate_key V:/privkey2.pem;
ssl_session_timeout 5m;
# Upgrade websocket requests and route the api backend
location ~ ^/(api|ws)/
{
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_http_version 1.1;
proxy_set_header Host $host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_pass http://127.0.0.1:8092;
}
location /
{
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
proxy_http_version 1.1;
proxy_pass http://127.0.0.1:8092;
}
}
server #catch 443 and https invalid requests before the wrong site is shown
{
listen 443;
server_name localhost;
ssl_certificate V:/fullchain2.pem;
ssl_certificate_key V:/privkey2.pem;
location /
{
error_page 404 /404.html;
}
error_page 404 /404.html;
# redirect server error pages to the static page /50x.html
#
error_page 500 502 503 504 /50x.html;
location = /50x.html
{
#root html;
}
}
server # Home Assistant Public redirect to https
{
listen 80;
server_name ha.[REDACTED].net;
return 301 https://$http_host$request_uri;
#location /
# {
# proxy_pass http://10.0.0.28:8123;
# proxy_buffering off;
# proxy_set_header X-Real-IP $remote_addr;
# proxy_set_header X-Forwarded-Host $host;
# proxy_set_header X-Forwarded-Port $server_port;
# proxy_set_header Upgrade $http_upgrade;
# proxy_set_header Connection “upgrade”;
# }
}
server # Home Assistant Internal Only redirect to https
{
listen 80;
server_name ha.hess;
location /
{
proxy_pass http://10.0.0.28:8123;
proxy_buffering off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection “upgrade”;
}
}
server #Plex Public redirect to https
{
listen 80;
server_name plex.[REDACTED].net;
return 301 https://$http_host$request_uri;
#gzip on;
#gzip_vary on;
#gzip_min_length 1000;
#gzip_proxied any;
#gzip_types text/plain text/css text/xml application/xml text/javascript application/x-javascript image/svg+xml;
#gzip_disable "MSIE [1-6]\.";
#
## Forward real ip and host to Plex
#proxy_set_header Host $host;
#proxy_set_header X-Real-IP $remote_addr;
##When using ngx_http_realip_module change $proxy_add_x_forwarded_for to '$http_x_forwarded_for,$realip_remote_addr'
#proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
#proxy_set_header X-Forwarded-Proto $scheme;
#proxy_set_header Sec-WebSocket-Extensions $http_sec_websocket_extensions;
#proxy_set_header Sec-WebSocket-Key $http_sec_websocket_key;
#proxy_set_header Sec-WebSocket-Version $http_sec_websocket_version;
#
## Websockets
#proxy_http_version 1.1;
#proxy_set_header Upgrade $http_upgrade;
#proxy_set_header Connection "Upgrade";
#
## Buffering off send to the client as soon as the data is received from Plex.
#proxy_redirect off;
#proxy_buffering off;
#
#location / {
# proxy_pass http://127.0.0.1:32400;
#}
}
server #Baserow Public
{
listen 80;
server_name br.[REDACTED].net;
return 301 https://$http_host$request_uri;
}
# another virtual host using mix of IP-, name-, and port-based configuration
#
#server {
# listen 8000;
# listen somename:8080;
# server_name somename alias another.alias;
# location / {
# root html;
# index index.html index.htm;
# }
#}
#server #Ispy Agent
# {
# listen 443 ssl http2;
# server_name nvr.[REDACTED].net;
# ssl_certificate V:/fullchain2.pem;
# ssl_certificate_key V:/privkey2.pem;
# ssl_session_timeout 5m;
# charset utf-8;
#
# location /
# {
# proxy_pass http://localhost:8095;
# proxy_buffering off;
# proxy_set_header X-Real-IP $remote_addr;
# proxy_set_header X-Forwarded-Host $host;
# proxy_set_header X-Forwarded-Port $server_port;
# }
# }
server #Plex Public
{
listen 443 ssl http2;
server_name plex.[REDACTED].net;
# path to fullchain.pem on local machine
ssl_certificate V:/fullchain2.pem;
# path to privkey.pem
ssl_certificate_key V:/privkey2.pem;
set $plex https://127.0.0.1:32400;
gzip on;
gzip_vary on;
gzip_min_length 1000;
gzip_proxied any;
gzip_types text/plain text/css text/xml application/xml text/javascript application/x-javascript image/svg+xml;
gzip_disable "MSIE [1-6]\.";
# Forward real ip and host to Plex
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
#When using ngx_http_realip_module change $proxy_add_x_forwarded_for to '$http_x_forwarded_for,$realip_remote_addr'
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Sec-WebSocket-Extensions $http_sec_websocket_extensions;
proxy_set_header Sec-WebSocket-Key $http_sec_websocket_key;
proxy_set_header Sec-WebSocket-Version $http_sec_websocket_version;
# Websockets
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
# Buffering off send to the client as soon as the data is received from Plex.
proxy_redirect off;
proxy_buffering off;
location / {
proxy_pass $plex;
}
}
server #Home Assistant Public
{
listen 443 ssl http2;
server_name ha.[REDACTED].net;
ssl_certificate V:/fullchain2.pem;
ssl_certificate_key V:/privkey2.pem;
charset utf-8;
location /
{
proxy_pass http://10.0.0.28:8123;
proxy_buffering off;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection “upgrade”;
}
}
server #Unifi Edge-OS Public
{
listen 443 ssl http2;
server_name [REDACTED].[REDACTED].net;
ssl_certificate V:/fullchain2.pem;
ssl_certificate_key V:/privkey2.pem;
ssl_session_timeout 5m;
charset utf-8;
location /
{
proxy_pass http://10.0.0.1;
proxy_buffering off;
#proxy_set_header X-Real-IP $remote_addr;
#proxy_set_header X-Forwarded-Host $host;
#proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection “upgrade”;
}
}
server #Baserow Public
{
listen 443 ssl http2;
server_name br.[REDACTED].net;
ssl_certificate V:/fullchain2.pem;
ssl_certificate_key V:/privkey2.pem;
ssl_session_timeout 5m;
# Upgrade websocket requests and route the api backend
location /
{
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
proxy_http_version 1.1;
proxy_pass http://127.0.0.1:8092;
}
location ~ ^/(api|ws)/
{
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_http_version 1.1;
proxy_set_header Host $host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_pass http://127.0.0.1:8092;
}
}
server #Baserow Internal Only
{
listen 443 ssl http2;
server_name br.hess;
ssl_certificate V:/fullchain2.pem;
ssl_certificate_key V:/privkey2.pem;
ssl_session_timeout 5m;
# Upgrade websocket requests and route the api backend
location ~ ^/(api|ws)/
{
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_http_version 1.1;
proxy_set_header Host $host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_pass http://127.0.0.1:8092;
}
location /
{
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
proxy_http_version 1.1;
proxy_pass http://127.0.0.1:8092;
}
}
}
Here is the Docker command I am currently using to create the container and I start it using the GUI in Docker for Desktop
docker run --name baserow -e BASEROW_PUBLIC_URL=https://br.[REDACTED].net -e WEB_FRONTEND_PORT=443 -e EMAIL_SMTP=True -e EMAIL_SMTP_USE_TLS=True -e EMAIL_SMTP_HOST=‘smtp.mail.yahoo.com’ -e EMAIL_SMTP_USER=’[REDACTED]’ -e EMAIL_SMTP_PORT=587 -e EMAIL_SMTP_PASSWORD=’[REDACTED]’ -v baserow_data:/baserow/data -p 127.0.0.1:8092:80 -p 587:587 -p 465:465 -p 8000:8000 --restart unless-stopped baserow/baserow:1.15.1
Chrome Network Log Headers Tab
Request URL: https://br.[REDACTED].net/api/user-files/upload-file/
Request Method: POST
Status Code: 413
Remote Address: 207.179.235.204:443
Referrer Policy: strict-origin-when-cross-origin
content-length: 585
content-type: text/html
date: Tue, 21 Mar 2023 21:15:50 GMT
server: nginx/1.23.3
:authority: br.[REDACTED].net
:method: POST
:path: /api/user-files/upload-file/
:scheme: https
accept: application/json
accept-encoding: gzip, deflate, br
accept-language: en-US,en;q=0.9
authorization: JWT eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0b2tlbl90eXBlIjoiYWNjZXNzIiwiZXhwIjoxNjc5NDMzODk5LCJpYXQiOjE2Nzk0MzMyOTksImp0aSI6IjEwNDhkZGI1NDJkMTQyNjU5ZDA5ZDdiOGRiZGVmYjhkIiwidXNlcl9pZCI6MX0.G24p92zqslDfTr-3Pco7TF5o_D18WmPwNFvaawThc2I
clientsessionid: 0ff5eba7-e062-4def-b276-af21c8e96f47
content-length: 10047349
content-type: multipart/form-data; boundary=----WebKitFormBoundaryjfUH8c4wv7MV1XCc
cookie: i18n-language=en; jwt_token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0b2tlbl90eXBlIjoicmVmcmVzaCIsImV4cCI6MTY3OTY5MTE2NCwiaWF0IjoxNjc5MDg2MzY0LCJqdGkiOiIwZWFmZGY5YmM5Nzk0MDAzOTk0ZjVhNDVhOWU1Yzg5NiIsInVzZXJfaWQiOjF9.mSz2HgYxeYKs-vSY81b3PUqCBcSqkd8dL4AZ9Bsftlw; baserow_group_id=186
origin: https://br.[REDACTED].net
referer: https://br.[REDACTED].net/database/189/table/678
sec-ch-ua: "Google Chrome";v="111", "Not(A:Brand";v="8", "Chromium";v="111"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
sec-fetch-dest: empty
sec-fetch-mode: cors
sec-fetch-site: same-origin
user-agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
websocketid: c98819c1-fd2c-4575-bb39-6c4bdcc4b584
Chrome Network Logs Response Tab
<html>
<head><title>413 Request Entity Too Large</title></head>
<body>
<center><h1>413 Request Entity Too Large</h1></center>
<hr><center>nginx/1.23.3</center>
</body>
</html>
<!-- a padding to disable MSIE and Chrome friendly error page -->
<!-- a padding to disable MSIE and Chrome friendly error page -->
<!-- a padding to disable MSIE and Chrome friendly error page -->
<!-- a padding to disable MSIE and Chrome friendly error page -->
<!-- a padding to disable MSIE and Chrome friendly error page -->
<!-- a padding to disable MSIE and Chrome friendly error page -->
Actually looking at it now it appears to be an Nginx issue but I have no clue how to fix that as I’m fairly new to Nginx.
The way my domain is configured is that I use Amazon AWS Route 53 for the domain name I own and there is a wildcard in the rotuing that unless otherwise specifed all requests are routed to the IP Address of my router. I do have an SSL Certificate that is issued by Let’s Encrpyt and renewed automatically by the Let’s Encrypt addon for Home Assistant and is accessible. over a dedicated file share for all machines that need it.
Side note email invites also do not work but I can work around that for my use case, but if it gets fixed in the troubleshooting for pictures not uploading then that’s great.